Hot off the Press: A PowerShell Malware Challenge
Hot off the Press is a malware CTF challenge from the 2023
Huntress CTF. This write-up walks through the initial discovery,
de-obfuscation, and solving of the challenge. The actual flag will be redacted
from the document, but interested parties should be able to follow the steps
and derive it themselves. While the write-up assumes a base level of knowledge
regarding the command line, Linux, cryptography, and PowerShell. Most tools and
commands will be accompanied by short explanations. This is a fun entry-level
malware reversal challenge that is completable by all entry-level cybersecurity
students with a little research.
Step 1: File Discovery
The file “hot_off_the_press” was given with the explanation
that this malware was from a news article. The article is about numerous
vulnerabilities targeting WS_FTP Server Ad Hoc Transfer Module within their
WS_FTP software.
Like most CTFs, this file didn’t have an extension telling
us what it was. The “file” command comes in handy here, telling us that it is
something called a UHARC archive.
It turns out that UHARC is an older compression software
that was last updated in 2009. The command line tool can be found at the
developer website https://sam.gleske.net/uharc/. After identifying the file as a UHARC archive
and installing the UHARC command line tool, the file can be renamed to include
the uha extension.
Then, the UHARC tool can be used to extract the file from
the archive.
The file that gets extracted
is a PowerShell script file.
Step Two: De-Obfuscation and Analysis
We can see that this file is
all in one line, which makes it hard to read. With something like this, we’ll
want to start separating the commands out into a more readable format. We can
see a distinction from the cmd.exe command and the powershell commands being
passed.
Something that sticks out here is that the switches passed to the powershell exe command are not complete. One quirk of PowerShell is that it auto-completes unfinished parameters. Attackers use this to obfuscate what commands they are running.
After spacing out the code a
little more, we have something that is a lot more readable and approachable. We
can see that the structure of the file is CMD execution of a PowerShell instance
which is then executing some kind of code.
Knowing this, we can start to
deobfuscate the code. I did this with the good ol’ find and replace. One of the
patterns I saw was that commands and strings were being joined with “+”, which
is a common way of joining things in PowerShell.
I also noticed that a lot of
commands were using string replacements as well. In PowerShell, using a -f
after a string will allow you to place characters in strings. Knowing this, I
also went through and fixed all the strings.
After fixing all the strings,
we’re left with something like this:
As we can see, there is a bunch of code and then a command executing a base64 string.
Using the find/replace tool in Notepad, I swapped out the brackets for their respective letters.
Putting this into CyberChef,
we get a result indicating that this is a Gzip archive.
Using CyberChef, we’re able
to download the detected file. This requires some security disabling because
Chrome doesn’t like you downloading malware. Defender may also hassle you here,
but we can just ignore it 😉
The file is identified as a
Trojan, so we’re on the right track!
Bringing the file back into
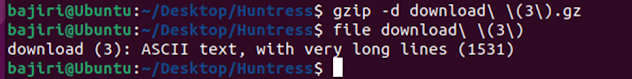
our Linux environment, we can run some commands on it to verify the type.
Once we know it is definitely
a Gzip archive, we can use Gzip to extract it.
Step Three: Solving
The file we get is another PowerShell script file. This one is not obfuscated outside of a single base64 string. This is interesting, and it doesn’t seem like the base64 string has any other layers of obfuscation on it.
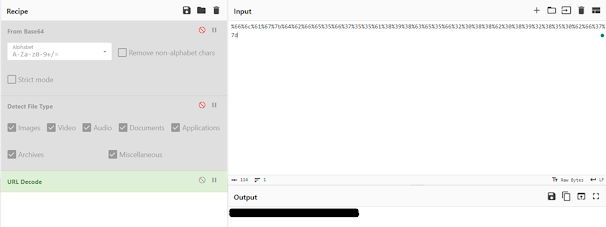
Popping the base64 line into CyberChef gets us an encoded URL.
Using CyberChef again, we can
decode the URL into the flag!

















Comments
Post a Comment