EDIT: Related video made for a class
For the testing environment, I have a Windows lab consisting of a 2012 AD, 2019 Email server, 2016 Docker/Hyper-V box, and Windows 10 and 7 machines. This setup is for CCDC prep and is designed to mirror the environments and machines used in the competition. I also have a kali box running on the same network as the Windows machines. This is what staged the attacks on the 2012 AD server.
To begin with, I had to do some research and reading on the exploit process and setup. Making sure that the systems hadn't been patched with KB4601357, the Microsoft update that solves the Netlogon vulnerabilities that allow the zerologon exploit to work, and pulling down the newest version of Impacket and the zerologon exploit script to the kali box.
Once the scripts and AD were ready to go, I started Wireshark on the AD server and got to executing the first steps of the exploit.
Step 1) Using the zerologon exploit script to set the machine password of the domain controller to be empty.
Step 3) Running wmiexec to establish an SMB connection using the credentials of the Administrator account.
Step 4) Using secretsdump again, this time with the registry values taken from the domain controller.
Step 5) Finally, we can restore the original password to the domain controller, leaving our presence largely unnoticed.
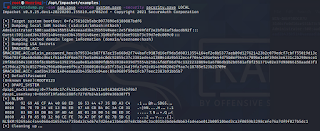
Here is the Wireshark capture from the AD machine.
In the end, we're left with the credentials for the domain administrator, which allows us to do just about anything we want to the victim. They likely wouldn't even know they had been hit with an attack. I certainly couldn't figure it out beyond some suspicious processes and packet traffic.
If this is the level of stuff we're seeing in the qualifiers, I'm looking forward to seeing what they hit us with in the next level. Being able to get hands-on with the systems and try to protect and respond to real-time threats has been a great learning experience. It's definitely a little hectic and crazy when you're seeing all these red flags appear and have no idea what's going on, but I love that feeling of excitement and the rush you get when you finally figure out what's happening and how to fix it. The red team definitely kept me on my toes during the competition, and I left with a huge list of things to learn and research further.
Now, it's time to start preparing for regionals. We're bringing it home!




Comments
Post a Comment